
Social Engineering - Phishing Emails: Part I
Social Engineering Phishing Social-Engineer Toolkit
Disclaimer: For educational purposes only.
According to IBM, Phishing is a type of cyberattack that uses fraudulent emails, text messages, phone calls or websites to trick people into sharing sensitive data, downloading malware or otherwise exposing themselves to cybercrime. Phishing attacks are a form of social engineering. Phishing is also the most common form of cyber crime, with an estimated 3.4 billion spam emails sent every day (source: AAG IT). In this blog post, we are going to learn how to serve a phishing website with a sign-in form and grab the user’s credentials.
Phishing attacks can be unethical, so they should only be conducted if you are in charge of a social engineering campaign by your employer or if it is a legally contracted social engineering service you are offering as a company or as a freelancer. That being said, this is an educational post that contains a small challenge. It doesn’t target any company and doesn’t provide the full steps to replicate a harmful campaign outside of a local testing environment. The goal is to understand at least how very basic versions of the attacks can be pulled off to better understand how to defend from them. In the future, I’ll also be providing some tips on how to identify phishing emails to complement this information.
For this experiment, we will be using the Social-Engineer Toolkit (SET) that comes pre-installed in Kali Linux. In case you don’t have it installed, please follow the install instructions in the official GitHub page.
Let’s start. Hop on a system with SET installed and follow the instructions:
- Run the tool with:
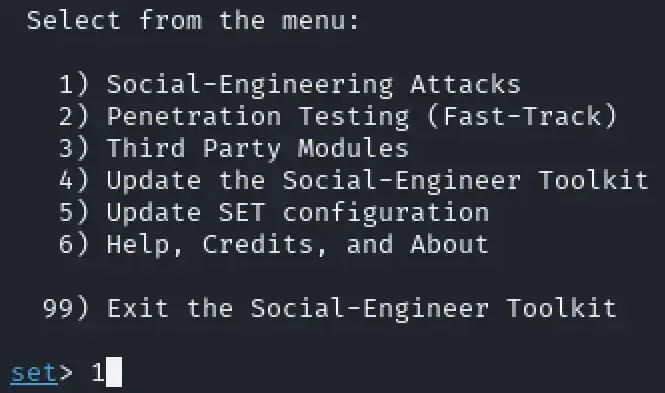
sudo setoolkit(or run it as root without sudo). - Now, just follow the prompts. Choose “Social-Engineering Attacks” in the first one:
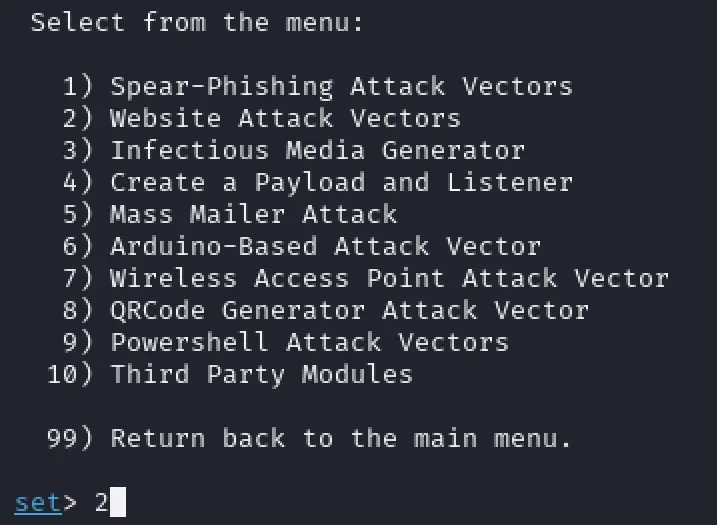
- Choose “Website Attack Vectors”:
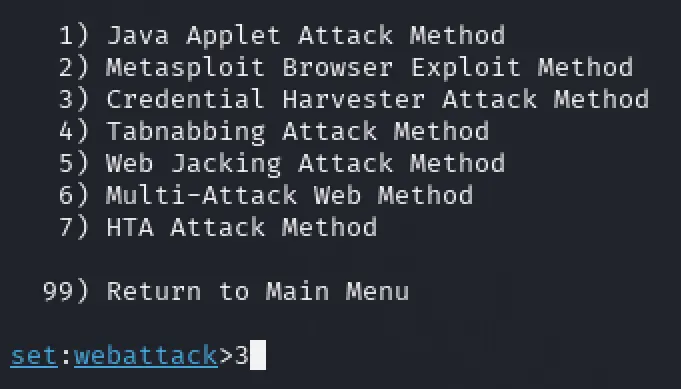
- Choose “Credential Harvester Attack Method”:
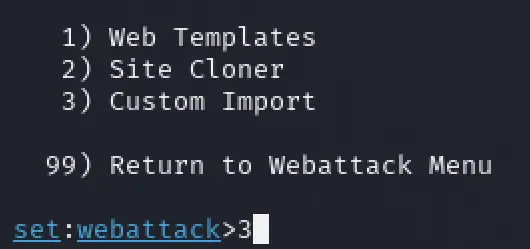
- Choose “Custom Import”. For this to work you will need a local copy of the website you intend to show. You can use tools like HTTrack to clone a website or you can even try to just copy the target HTML of the page to a local folder and name it index.html. More on this later.
After choosing that option you’ll be asked:
- For an IP address: This is the IP address of the machine where you are hosting the phishing site. Choose an IP that is reachable by your target(s) preceding it by “http://”, e.g.
http://192.168.1.2. I made this test hosting the phishing page on a VM and accessing it on a physical machine, both inside my home network. Never expose your home’s public IP. Also, shorten the URL before sending it to your target(s) with a service like URL shortened or bitly. - For the path to the website: this is the path in the local file system to the folder containing the code of the cloned website. Tested with an absolute path to the folder and it worked.
- If you want to copy the entire folder or just index.html: If the site appears unformatted using only the index.html, go with the entire folder option.
- For the URL of the website you cloned: This is the URL of the real website. It will be used to redirect users to it after they “sign-in” using your fake form.
After everything is set-up, test the link and sign-in using the form. You should be able to see the typed in credentials in your terminal:

Challenge:
As you probably noticed, there is an option called “Site Cloner” that can be used instead of a “Custom Import”. Try it and see the results, you might not be able to see the credentials in plain text in your terminal. This type of attack is so widespread and so easy to pull-off that companies started applying some protections to prevent, at least non-technical people, to successfully pull it off just by following a simple tutorial on the Web. For it to work for me, I needed to download the HTML of the target page and edit it to remove those protections. Play around with it, and maybe ask, at your company, if you can start raising awareness against email phishing attacks with a simulation.
In Part II, I’ll explain how to send emails, that don’t end up in the spam folder, with the link to the phishing page.
If you find the website useful, please feel free to share it on social media and get in touch!