
Social Engineering - Phishing Emails: Part III
Social Engineering Phishing SOC VirusTotal
In this series, we already learned how to create a fake phishing website and how to send an email with a link to open it. But how can we differentiate a phishing email from a regular legitimate email?
The following tips are just a subset of a more in-depth analysis a SOC analyst would do but should already be useful to spot plenty of phishing attempts.
Obvious Red Flags
Did you receive an email from a Nigerian prince saying you just won a million bucks? Did you receive an email with a big sense of urgency to change a password or to verify an account? Are you being blackmailed to transfer a large sum of money? Is someone going to arrest you if you don’t transfer him or her some money?
While some of the requests above are obvious malicious attempts, it might not always be that easy to spot a phishing email. Take the example below, shared by Thomas Ballin on LinkedIn:
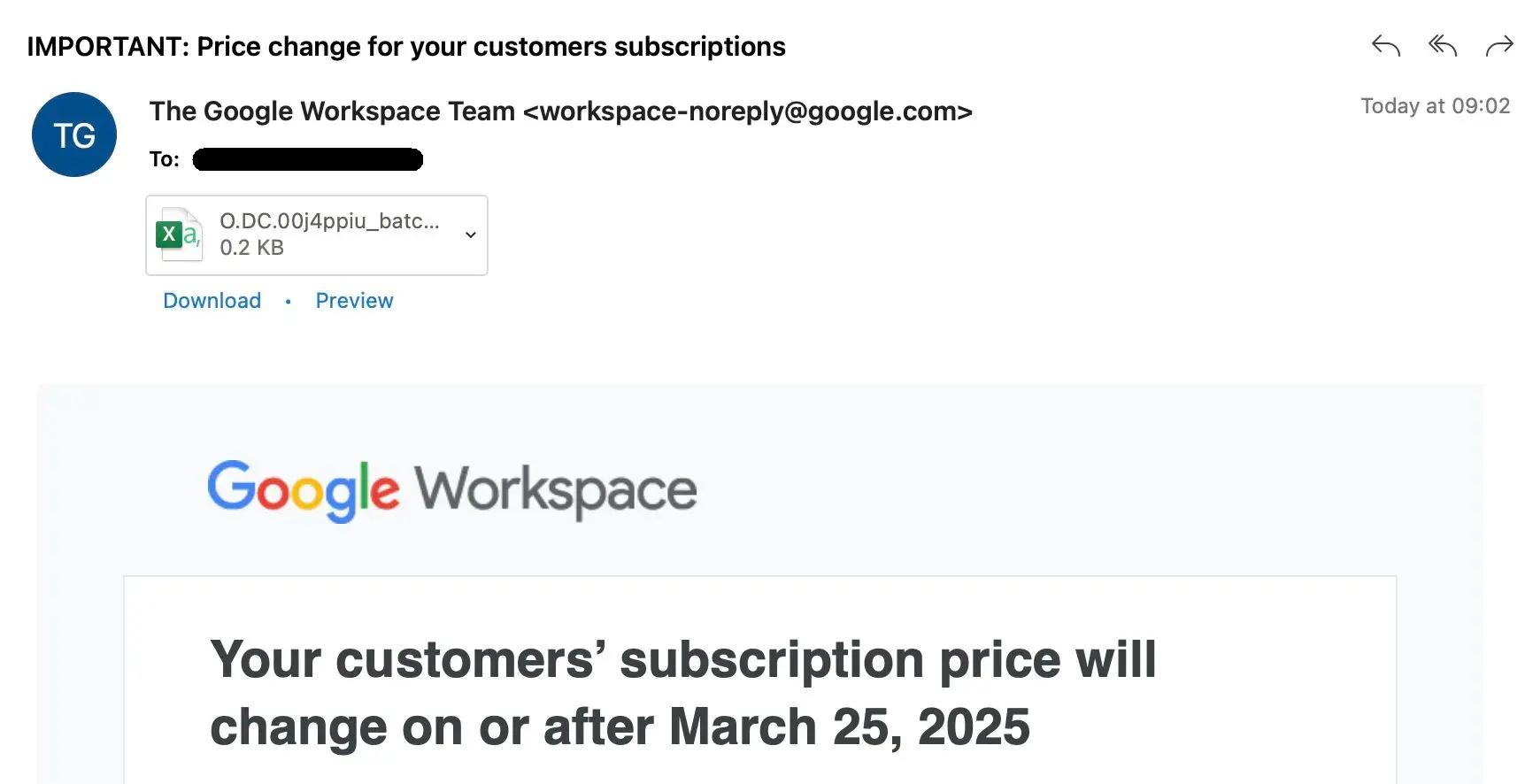
Yes it legitimate, or phishing? I honestly have no idea without further analysis. Only the attachment name looks phishy.
Analyse the Email
Download the email into a folder and do not click in any link. Open the source code and take a look into:
- The sender: does it use a suspicious email? Sometimes it might be very close to a legitimate one, e.g. googlechecking.com or microsoftinfo.org. Check VirusTotal to see if any vendor already reported the link as malicious.
- Analyse the Sender IP with the WHOIS tool. You might find that the IP doesn’t belong to the expected organization.
- Download the attachment (do not open it) in a virtual machine and upload it to VirusTotal for further analysis.
Defensive Actions
Imagine you just analysed an email and have confirmed it as a phishing attempt. What are the next steps?
Immediately create a filter to block the sender’s email address and add rules to any firewall to block the IP. Inform the rest of the team of the phishing attempt.
Provide guidance and awareness on how to detect phishing emails. In my opinion, phishing cannot be fully nullified but some attempts are just silly and might work if there is no security awareness in your corp.
Plenty of cybersecurity attacks start from the “inside”. A lot of security incidents begin because an employee clicked on a link. Did you think twice before clicking this link? If yes, good!
Recommended courses
If you wish to learn more about the subject I recommend the Practical Phishing Campaigns Course from TCM Security.
If you find the website useful, please feel free to share it on social media and get in touch!